Helpful Threat Hunting Scripts
Tricks and Tips YOU can use with threat hunting tools
By Liza Tsibur
Make it easier to find the bad guys!
Clean up the output!
More than one way to solve a problem!
RITA
By default, RITA produces comma-separated output. While this format is efficient, the lack of whitespace can make it challenging to read.
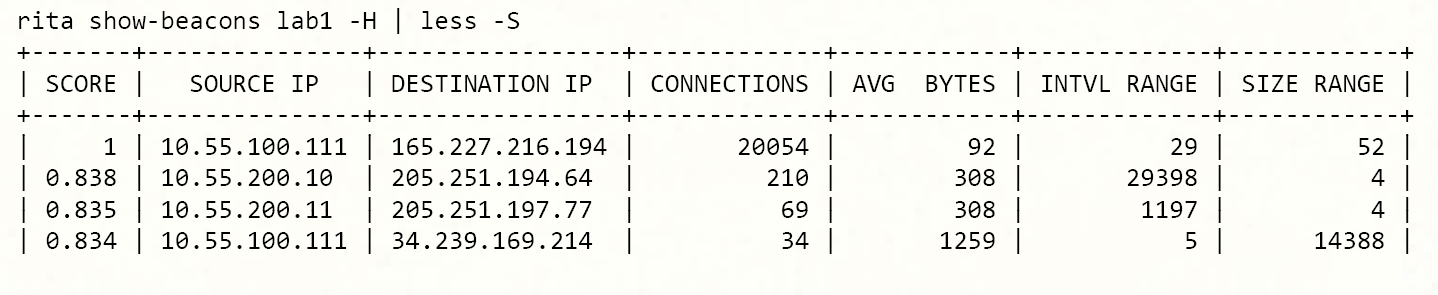
rita show-beacons lab1 | head -5Score,Source IP,Destination IP,Connections,Avg. Bytes,Intvl Range,Size Range,Top Intvl,Top Size,Top Intvl Count,Top Size Count,Intvl Skew,Size Skew,Intvl Dispersion,Size Dispersion,Total Bytes1,10.55.100.111,165.227.216.194,20054,92,29,52,1,52,7774,20053,0,0,0,0,18450200.838,10.55.200.10,205.251.194.64,210,308,29398,4,300,70,109,205,0,0,0,0,648500.835,10.55.200.11,205.251.197.77,69,308,1197,4,300,70,38,68,0,0,0,0,213130.834,10.55.100.111,34.239.169.214,34,1259,5,14388,1,156,15,30,0,0,0,0,42831Adding ASCII Formatting
You can use the “-H” switch to add some ASCII formatting to the RITA output. Piping the output through “less -S” will avoid line wrapping.
Redirect RITA HTML Output
RITA’s “html-report” option outputs data into a series of webpages. This makes it easier to browse the output using a web browser. The problem is RITA defaults to creating the HTML files under the current directory. What if you want to place the files somewhere else? Create a one line script with the following entry:
(cd /var/www/html; rita html-report $1)Now when you run the script, you simply specify the dataset you want to see in HTML format. Rather than creating the files in the current location, they will be created under “/var/www/html”.
Excluding Previously Hunted IPs from RITA
RITA does not support safelisting to remove previously hunted IPs. However, you can work around this by piping the output through “grep.” You will want to use grep with the following switches:
-v = Print all lines that do not match the specified pattern
-F = Match as a fixed string
-w = Only match when pattern has white space before and after
-f = Load match entries from a file
Next, add the IP addresses you have previously hunted to a file, one per line. For this example, we’ll name the file “exception.txt”. Now it’s a simple matter of redirecting the RITA output through the grep command:
rita show-beacons lab1 | grep -v -w -F -f exception.txtThe final output will contain beacon data for every IP address except for the ones you have listed in the exception.txt file.
Quick Info Dump
When you want to investigate an IP address or fully qualified domain name (FQDN), Zeek can provide helpful information, which is spread across multiple files. Here’s a handy script:
echo ‘DNS info’cat dns.* | zeek-cut answers query | sort | uniq | grep -Fw $1echo ‘HTTP info’cat http.* | zeek-cut id.resp_h host user_agent | sort | uniq | grep -Fw $1echo ‘TLS info’cat ssl.* | zeek-cut id.resp_h server_name validation_status | sort | uniq | grep -Fw $1When you run the script followed by an IP address or FQDN, it will search multiple files and print out identification data. If no data is present, the script simply prints a blank line. If your logs are in compressed format, use “zcat” instead of “cat”.
Getting Totals With “sort | uniq -c | sort -rn”
In many cases, you may want to identify the quantity of an attribute that has been seen on the network. For example: which IP pairs created the greatest number of connections? Which internal system sent the most data to the internet? Which IP pairs generated the longest duration connections? Using sort and uniq can help you quickly total these values.
sort | uniq | sort Examples
To see the top 10 IP pairs that are creating the most number of connections:
zeek-cut id.orig_h id.resp_h | sort | uniq -c | sort -rn | headTop 10 user agent strings seen on the network:
cat http.log | zeek-cut user_agent | sort | uniq -c | sort -rn | headThe “-k” switch can be used with sort to change the column used for sorting. For example, to identify the top 10 longest duration connections when the duration field is in the third column, you can run the command:
zeek-cut id.orig_h id.resp_h duration | sort -k3 -rn | headIt can also be useful to pipe the output through additional tools prior to presenting it. For example, what if we wanted to see the longest cumulative communication time between each pair of IP addresses? We can’t extract that data directly, as there may be multiple connections between IP pairs that need to be added together. Datamash can be used to add values in a column. Here’s an example:
cat conn.log | zeek-cut id.orig_h id.resp_h duration | sort | datamash -g 1,2 sum 3 | sort -k 3 -rn | headIn this example, datamash will add up (sum) all of the values in the third column (duration) when the values in the first two columns (-g 1,2) are the same. Note that we could easily script this command to reduce the amount of typing that is required each time we wish to run it.